Ugly firewall
Table of contents
Ugly Firewall
This is mi scripts to manage linux netfilter iptables, i tried to do not install 3th tools that can’t do what i want, are ultra complicated, or need compiled code to run as binarys files, adding more layers to netfilter tools. It is easy to read a simple bash script to see what it do, and only with few lines of code (less than 200) and some organized files we can manage our firewall in linux.
There isn’t a tool/script to manage iptables whitout know how iptables works, to make custom rulescripts to load it is hight recomended to learn a few of iptables.
How it works
Macking some user chains like LOG-ACCEPT-OUTPUT to jump in when packet match and grep only rules with our LOG- prefix to show status.
A base rulescript file that can be customized with our own policy to drop all, permit only loopback, permit only output packeds, etc.
Some custom user rulescript files like iptables.output.http.https.dns.uf.sh to easy load fast some prebuild rules we need.
And more.
Getting Started
These instructions will get you a copy of the project.
Installing
git clone https://github.com/VielLosero/ugly-firewall.git
root@kali:~/data/git-repos/vielLosero# git clone https://github.com/VielLosero/ugly-firewall.git
Clonando en 'ugly-firewall'...
remote: Enumerating objects: 4, done.
remote: Counting objects: 100% (4/4), done.
remote: Compressing objects: 100% (4/4), done.
remote: Total 4 (delta 0), reused 0 (delta 0), pack-reused 0
Desempaquetando objetos: 100% (4/4), listo.
Running ugly-firewall
After cloning the repository change to ugly-firewall dir and run ./uf
Or make a link for easy run: ln -s PATH/ugly-firewall/uf /usr/bin/fw
root@kali:~# cd ugly-firewall/
root@kali:~/ugly-firewall# ./uf
root@kali:~# fw
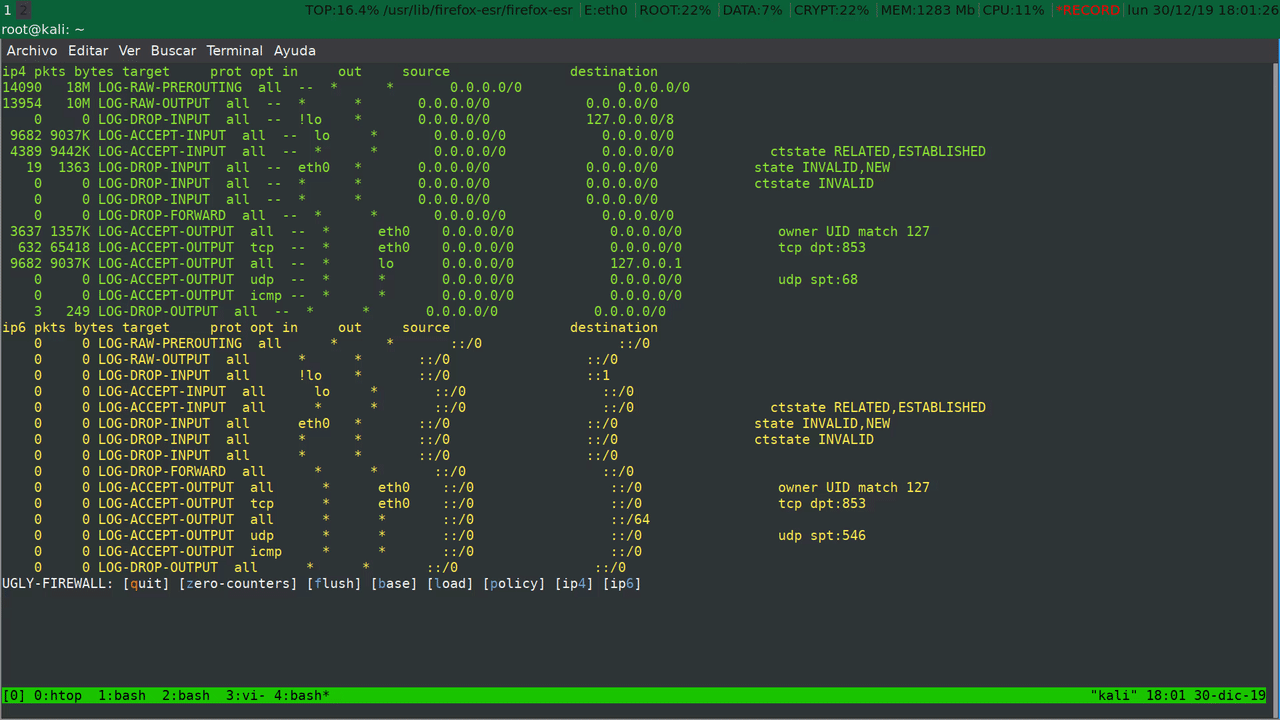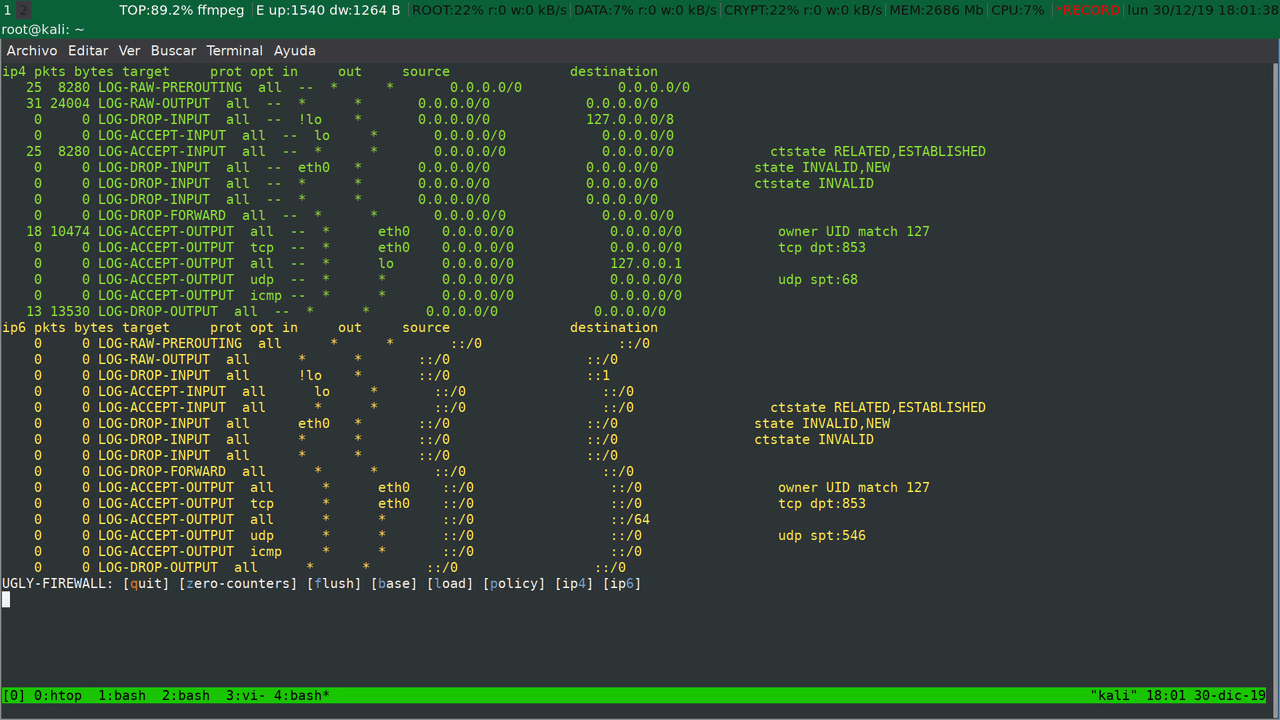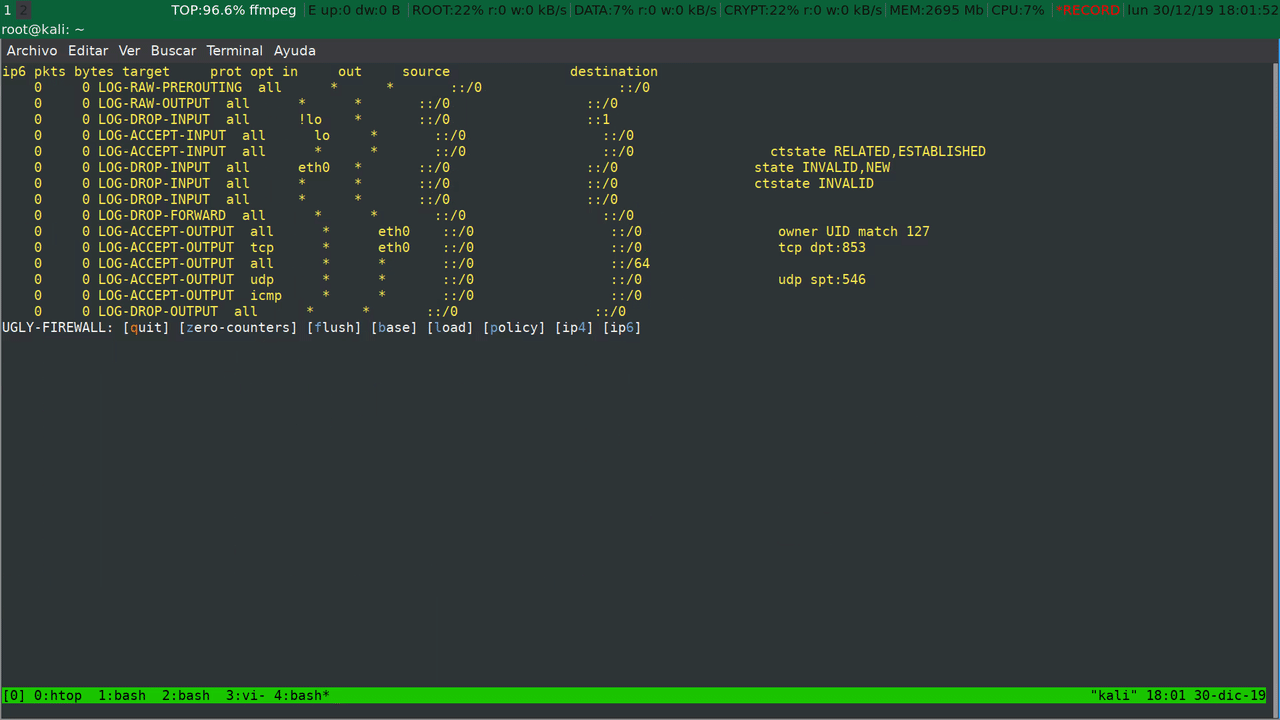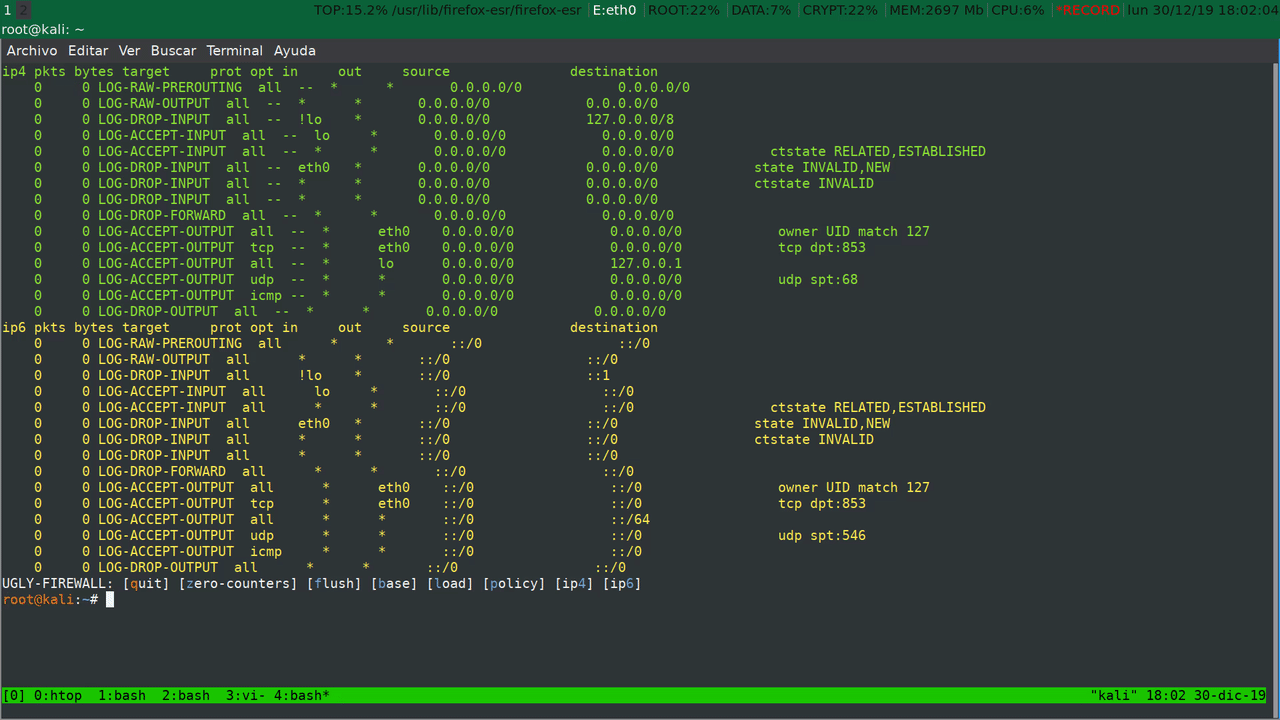
Output While Running
ip4 pkts bytes target prot opt in out source destination
7002 9017K LOG-RAW-PREROUTING all -- * * 0.0.0.0/0 0.0.0.0/0
6784 5298K LOG-RAW-OUTPUT all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 LOG-DROP-INPUT all -- !lo * 0.0.0.0/0 127.0.0.0/8
4103 4326K LOG-ACCEPT-INPUT all -- lo * 0.0.0.0/0 0.0.0.0/0
2899 4692K LOG-ACCEPT-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 LOG-DROP-INPUT all -- eth0 * 0.0.0.0/0 0.0.0.0/0 state INVALID,NEW
0 0 LOG-DROP-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 LOG-DROP-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 LOG-DROP-FORWARD all -- * * 0.0.0.0/0 0.0.0.0/0
2041 661K LOG-ACCEPT-OUTPUT all -- * eth0 0.0.0.0/0 0.0.0.0/0 owner UID match 127
254 24774 LOG-ACCEPT-OUTPUT tcp -- * eth0 0.0.0.0/0 0.0.0.0/0 tcp dpt:853
4103 4326K LOG-ACCEPT-OUTPUT all -- * lo 0.0.0.0/0 127.0.0.1
0 0 LOG-ACCEPT-OUTPUT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:68
0 0 LOG-ACCEPT-OUTPUT icmp -- * * 0.0.0.0/0 0.0.0.0/0
386 286K LOG-DROP-OUTPUT all -- * * 0.0.0.0/0 0.0.0.0/0
ip6 pkts bytes target prot opt in out source destination
30 3078 LOG-RAW-PREROUTING all * * ::/0 ::/0
31 3134 LOG-RAW-OUTPUT all * * ::/0 ::/0
0 0 LOG-DROP-INPUT all !lo * ::/0 ::1
30 3078 LOG-ACCEPT-INPUT all lo * ::/0 ::/0
0 0 LOG-ACCEPT-INPUT all * * ::/0 ::/0 ctstate RELATED,ESTABLISHED
0 0 LOG-DROP-INPUT all eth0 * ::/0 ::/0 state INVALID,NEW
0 0 LOG-DROP-INPUT all * * ::/0 ::/0 ctstate INVALID
0 0 LOG-DROP-INPUT all * * ::/0 ::/0
0 0 LOG-DROP-FORWARD all * * ::/0 ::/0
0 0 LOG-ACCEPT-OUTPUT all * eth0 ::/0 ::/0 owner UID match 127
0 0 LOG-ACCEPT-OUTPUT tcp * eth0 ::/0 ::/0 tcp dpt:853
30 3078 LOG-ACCEPT-OUTPUT all * * ::/0 ::/64
0 0 LOG-ACCEPT-OUTPUT udp * * ::/0 ::/0 udp spt:546
0 0 LOG-ACCEPT-OUTPUT icmp * * ::/0 ::/0
1 56 LOG-DROP-OUTPUT all * * ::/0 ::/0
UGLY-FIREWALL: [quit] [zero-counters] [flush] [base] [load] [policy] [ip4] [ip6]
Options
UGLY-FIREWALL: [quit] [zero-counters] [flush] [base] [load] [policy] [ip4] [ip6]
- q quit
- z reset counters
- f delete all rules and chains
- b load prebuild base rules
- l load additional user rules
- p policy menu
- 4 show/hide ip4
- 6 show/hide ip6
- r undocumented: list iptables rules
How to make rulescripts
- We need a bash script file that load the ugly-firewall config file:
#!/bin/bash
source $(dirname $0)/uf.config.sh
- with the iptables rules we desire, for example:
$iptables -I OUTPUT 1 -o $out_int -j LOG-ACCEPT-OUTPUT
$ip6tables -I OUTPUT 1 -o $out_int -j LOG-ACCEPT-OUTPUT
- and save it in the ugly-firewall directory with the name we want ended with “.uf.sh” so that uglu-firewall can find it and be available in the loading menu.
iptables.output.accept.all.uf.sh
Extra config
To see or change available interfaces edit uf.config.sh
To see or change available LOG-RULES edit iptables.log.sh
Contributing and support
Please read Contributor covenant for details, and code of conduct before submitting pull requests or issues.
If you want to support this project with a donation, here is mi Bitcoin address:
bc1q6d245chm8t5sdkqjugwg3ce2c92m276ee4ksv4
All donations are appreciated!
Author
- Viel Losero - Initial work - Viel Losero
back
References:
Licence: CC-BY-SA
